How to protect your PC from the major Meltdown and Spectre CPU flaws

A pair of nasty CPU flaws exposed this week have serious ramifications for home computer users. Meltdown and Spectre let attackers access protected information in your PC’s kernel memory, potentially revealing sensitive details like passwords, cryptographic keys, personal photos and email, or anything else you’ve used on your computer. It’s a serious flaw. Fortunately, CPU and operating system vendors pushed out patches fast, and you can protect your PC from Meltdown and Spectre to some degree.
It’s not a quick one-and-done deal, though. They’re two very different CPU flaws that touch every part of your operating system, from hardware to software to the operating system itself. Check out PCWorld’s Meltdown and Spectre FAQ for everything you need to know about the vulnerabilities themselves. We’ve cut through the technical jargon to explain what you need to know in clear, easy-to-read language. We’ve also created an overview of how the Spectre CPU bug affects phones and tablets.
The guide you’re reading now focuses solely on protecting your computer against the Meltdown and Spectre CPU flaws.
Editor’s note: This article was last updated to remove a link to direct downloads of the Windows Meltdown patch, mention how some AMD systems are becoming unbootable after installing it, and add performance impact estimates from Microsoft.
How to protect your PC against Meltdown and Spectre CPU flaws
Here’s a quick step-by-step checklist, followed by the full process.
- Update your operating system
- Check for firmware updates
- Update your browser
- Keep your antivirus active
First, and most important: Update your operating system right now. The more severe flaw, Meltdown, affects “effectively every [Intel] processor since 1995,” according to the Google security researchers that discovered it. It’s an issue with the hardware itself, but the major operating system makers have rolled out updates that protect against the Meltdown CPU flaw.
Brad Chacos/IDG
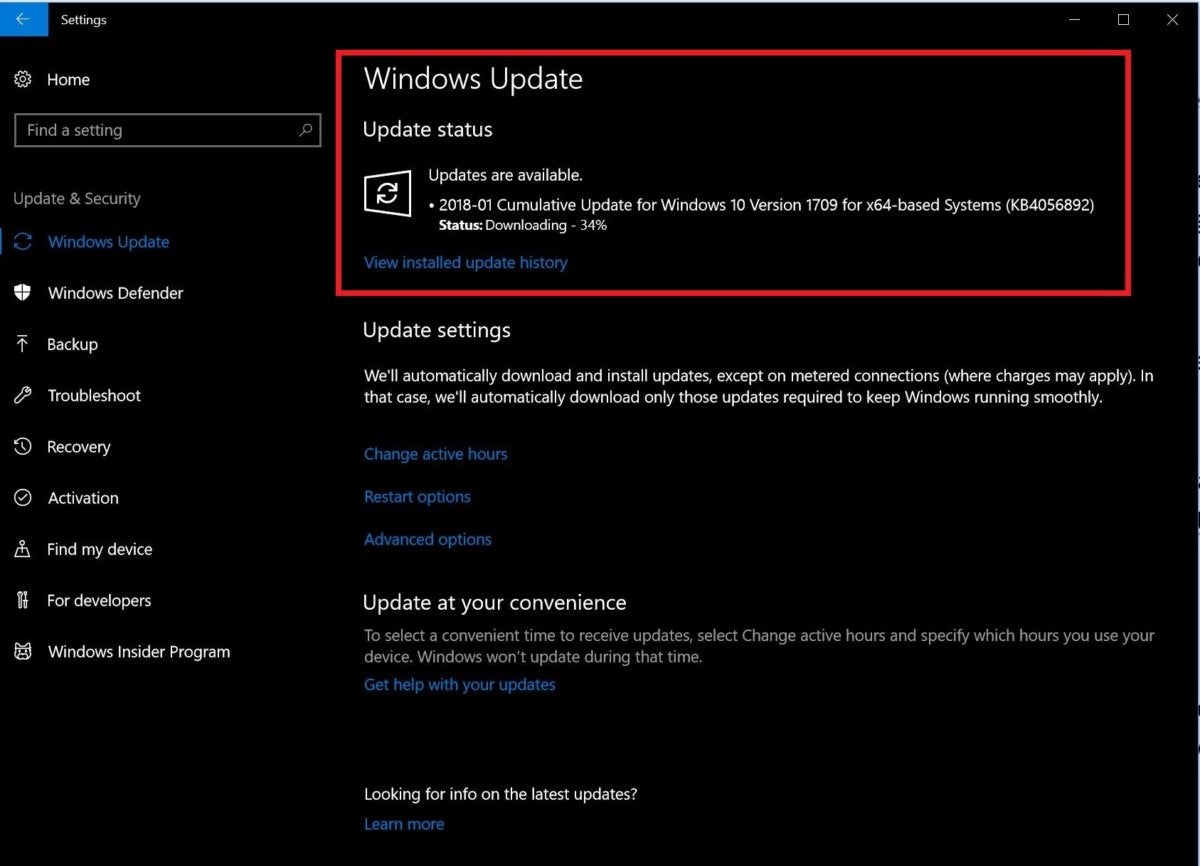
Microsoft pushed out an emergency Windows patch late in the day on January 3. If it didn’t automatically update your PC, head to Start > Settings > Update & Security > Windows Update, then click the Check now button under “Update status.” (Alternatively, you can just search for “Windows Update,” which also works for Windows 7 and 8.) Your system should detect the available update and begin downloading it. Install the update immediately.
You might not see the update, though. Some antivirus products aren’t playing nice with the emergency patch, causing Blue Screens of Death and boot-up errors. Likewise, the Meltdown patch renders some AMD computers unbootable, which forced Microsoft to halt its roll-out of the fix to potentially impacted systems. Because of the barrage of severely system-breaking errors, we do not recommend manually installing the Windows Meltdown patches if Microsoft hasn’t pushed them to your PC via Windows Update. We aren’t even going to link to the download page for the Meltdown updates. Don’t do it.

Google/Natascha Eibl
Apple quietly worked Meltdown protections into macOS High Sierra 10.13.2, which released in December. If your Mac doesn’t automatically apply updates, force it by going into the App Store’s Update tab. Chromebooks should have already updated to Chrome OS 63 in December. It contains mitigations against the CPU flaws. Linux developers are working on kernel patches. Patches are also available for the Linux kernel.
Now for the bad news. The operating system patches will slow down your PC, though the extent varies wildly depending on your CPU and the workloads you’re running. Intel expects the impact to be fairly small for most consumer applications like games or web browsing, and initial testing supports that, and reveals storage speeds can take a significant dip. Microsoft says Windows 10 PCs with Skylake (Core 6xxx series) chips or newer shouldn’t see much performance impact; Windows 10 PCs with 2015-era or older Intel processors “show more significant slowdowns”; and on Windows 7 and 8 systems with older Intel CPUs, Microsoft “expects most users to notice a decrease in system performance.”
You still want to install the updates for security reasons.
Check for a firmware update

Gordon Mah Ung
Because Meltdown’s CPU exploits exist on a hardware level, Intel is also releasing firmware updates for its processors. “By the end of next week, Intel expects to have issued updates for more than 90 percent of processor products introduced within the past five years,” it said in a statement on January 4.
Actually getting those firmware updates is tricky, because firmware updates aren’t issued directly from Intel. Instead, you need to snag them from the company that made your laptop, PC, or motherboard—think HP, Dell, Gigabyte, et cetera. Because of that, patches for individual systems will likely take longer than Intel’s stated week to trickle down to home users. Most prebuilt computers and laptops have a sticker with model details somewhere on their exterior. Find that, then search for the support page for your PC or motherboard’s model number.
Update your browser
You also need to protect against Spectre, which tricks software into accessing your protected kernel memory. Intel, AMD, and ARM chips are vulnerable to Spectre to some degree. Software applications need to be updated to protect against Spectre. The major PC web browsers have all issued updates as a first line of defense against nefarious websites seeking to exploit the CPU flaw with Javascript.
Brad Chacos/IDG
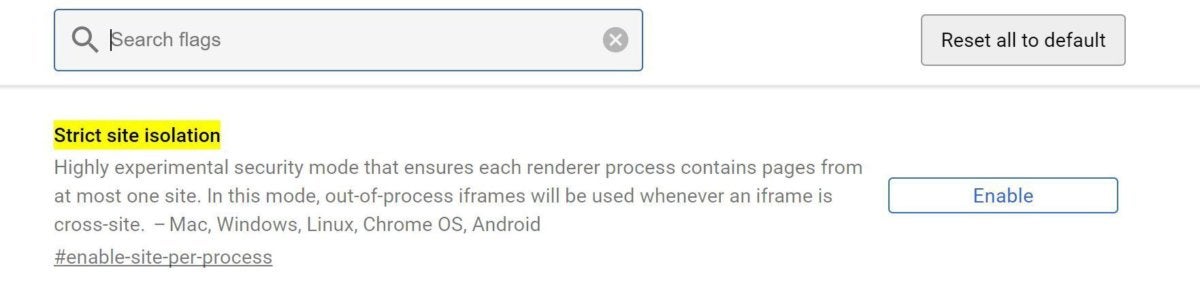
Microsoft updated Edge and Internet Explorer alongside Windows 10. Firefox 57 also wraps in some Spectre safeguards. Chrome 63 made “Site Isolation” an optional experimental feature. You can activate it right now by entering chrome://flags/#enable-site-per-process into your URL bar, then clicking Enable next to “Strict site isolation.” Chrome 64 will have more protections in place when it launches on January 23.
On January 8, Apple pushed out updates to iOS 11 and macOS with “security improvements to Safari and WebKit to mitigate the effects of Spectre.”
Keep your antivirus active
Finally, this ordeal underlines how important it is to keep your PC protected. The Google researchers who discovered the CPU flaws say that traditional antivirus wouldn’t be able to detect a Meltdown or Spectre attack. But attackers need to be able to inject and run malicious code on your PC to take advantage of the exploits. Keeping security software installed and vigilant helps keep hackers and malware off your computer. Plus, “your antivirus may detect malware which uses the attacks by comparing binaries after they become known,” Google says.
PCWorld’s guide to the best antivirus for Windows PCs can help you find the best option for your setup.
This story, “How to protect your PC from the major Meltdown and Spectre CPU flaws” was originally published by PCWorld.




